What’s the Future of Cybersecurity Content Gatekeeping?

Key takeaways
Rethinking how to engage with your cybersecurity audience
For years, the concept of “gatekeeping” content—requiring users to provide their information before accessing resources—has been on the decline. AI-driven search results, which deliver instant answers without forms or downloads, have accelerated this shift. Meanwhile, publishers are facing staff cuts, and media companies are rethinking how to engage audiences.
Some are doubling down on newsletters and podcasts, while others are redesigning their user experiences to mimic the addictive scroll of social media.
In B2B cybersecurity, this evolution is even more pronounced. Product marketing materials, white papers, thought leadership content, and research reports are abundant. As a result, traditional gated PDFs like case studies and analyst papers are struggling to capture leads. The obvious question arises: Is gatekeeping dead?
Not entirely. Gatekeepers have always played a vital role in filtering out noise—but to do it today, you must first establish extraordinary credibility. People will only request for you to “open the gate” if they trust that what’s inside is genuinely valuable.
So how can cybersecurity marketers continue to gate content effectively in this new era?
Host exclusive events
One of the most reliable ways to earn a prospect’s email is through high-profile, invite-only events. Whether it’s an executive roundtable or a virtual summit featuring industry thought leaders, exclusivity remains a powerful motivator.
Need ideas?
Here are five creative, invite-only digital cybersecurity marketing event concepts that are worth gating because they deliver exclusive value and position your brand as a trusted insider resource—going beyond the typical webinar format which while still dependable, could use some supplementation:
1. Cyber Threat Intelligence Roundtable
An exclusive, small-group session where security leaders exchange insights on emerging threats and real-world attack trends. Attendees collaborate on response strategies and participate in an interactive red team vs. blue team scenario.
2. Executive Cyber Crisis Simulation
A live, interactive tabletop exercise that walks participants through the pressures of responding to a major cyber incident. Attendees leave with actionable strategies and lessons from seasoned incident responders.
3. Cybersecurity Innovation Preview Lab
Gain early access to cutting-edge cybersecurity research, tools, and product innovations before they hit the market. This insider session includes direct interaction with the experts shaping next-generation defenses.
4. Threat Actor AMA (Ask-Me-Anything)
A rare opportunity to hear from ethical hackers and threat researchers about how attackers think and operate. Attendees can submit real security questions for live, unfiltered answers.
5. CISO Confidential Fireside Series
A closed-door discussion under Chatham House Rule where top CISOs share how they’re prioritizing risks and making buying decisions. Each session explores candid, actionable insights you won’t find in public forums.
The common thread that makes these events worth gating is exclusivity, personalization, and interaction you can’t get from AI search results
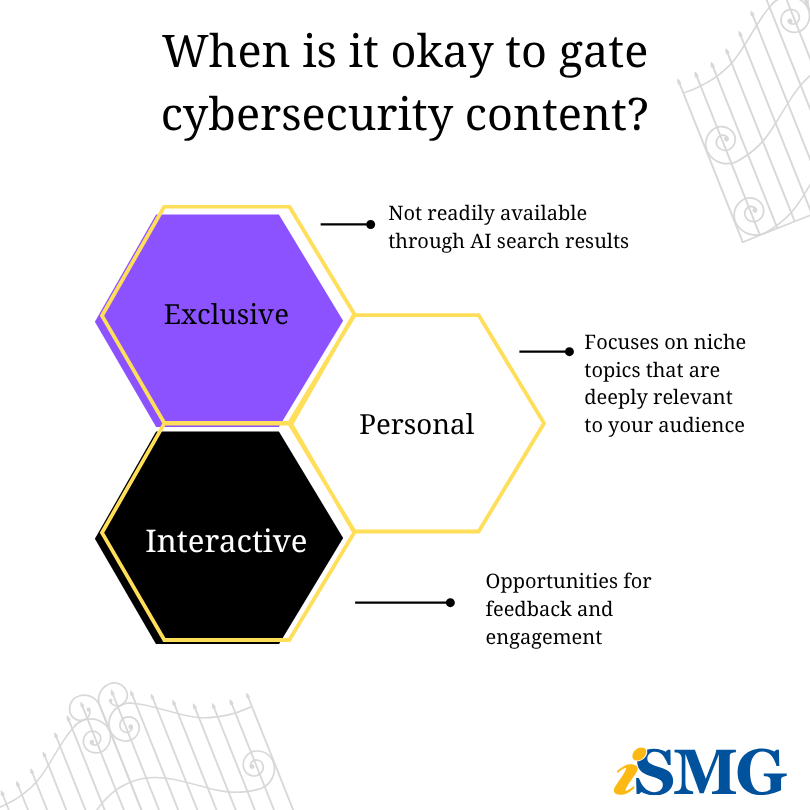
Build true communities
Buyers are more likely to share their contact information in exchange for access to a real community—one where their voices are heard, experts are accessible, and networking opportunities are tangible. A Slack group with no engagement doesn’t cut it; meaningful interaction is the new currency of trust.
What should your community provide?
- Connection and networking with executives sharing similar interests
- Learning experiences are prioritized over sales pitches
- A real world sandbox to test your ideas
- A safe space to share information
Offer practical, powerful tools
Content alone is less compelling than utility. Free tools, templates, or frameworks that immediately impact a prospect’s workflow are highly “gateworthy.” If your tool can save time, improve security posture, or simplify reporting, users will gladly trade an email address for access.
We recently discussed free tools in our blog
If you’re considering this strategy, make sure to understand the risks of having your leads not convert to sales opportunities.
Here are some important considerations:
- Align Teams on Freemium Goals: Create a cross-functional task force (marketing, product, sales) to define the free tier’s scope. For example, limit the free version to basic scans or single-device protection, reserving advanced features like real-time threat intelligence or multi-device coverage for paid tiers. This ensures marketing drives pipeline while sales can position premium value.
- Leverage Behavioral Data: Use telemetry to track how free users engage. If 80% of users stick to basic features like malware scanning, upsell advanced analytics or compliance tools. Segment users by intent (e.g., hobbyists vs. SMBs) for targeted campaigns, ensuring leads are qualified, as I learned was critical in my experience.
- Implement Time or Usage Limits: A time-bound trial (e.g., 30 days) or usage cap (e.g., five scans per month) creates urgency. For instance, Sophos offers a 30-day free trial of its endpoint protection, driving 15% conversion rates by nudging users to commit.
- Educate on Premium Value: Combat commoditization with clear messaging. Use in-app prompts or emails to showcase case studies of paid users thwarting sophisticated attacks, reinforcing why premium tiers are worth it in a trust-driven market.
- Experiment and Iterate: Test different freemium configurations. Try a standalone tool (e.g., a free browser extension for phishing detection) that complements but doesn’t undermine your core platform. Alternatively, offer a low-priced tier requiring a credit card, signaling commitment. As I found, emails to paying users (even at $5/month) carry more weight than those to free users, fostering trust and perceived value.
Marketing hack: use a trusted digital gate
If you don’t have the time or infrastructure to build credibility from scratch, consider leveraging trusted media networks like ISMG. With an established subscriber base and the ability to discreetly monitor audience interests, ISMG can help you target the right decision-makers. Pairing content syndication with Athena Intent signals ensures that your gated offers reach the people actively researching your topics.
Gatekeeping isn’t dead—it’s just evolving. The winners in cybersecurity marketing will be those who combine trust, exclusivity, and real value to make every “gate” worth opening.
