Why Cybersecurity Marketers Need Better Intent Data to Survive

Success begins with contact level intelligence
Top-of-funnel (TOFU) marketing in cybersecurity can get financially dangerous. It’s easy to spend a million dollars on an awareness campaign and walk away with little more than vanity metrics—impressions, clicks, maybe a few form fills. Even if you successfully acquire new marketing qualified marketing leads (MQLS), they often lack useful data about buying intent.
It’s nice to have an endless supply of highly-trained SDRs qualifying your marketing leads, but the process can get inefficient and expensive without enough context at the contact level.

Poor lead data gets you branded as that annoying marketer sending generic scripts without the necessary context or personalization to win buyer trust.
Contact level intelligence, reveals who’s actively researching solutions on a more granular level, all the way down to niche topics in the cybersecurity ecosystem. While there are plenty of intent providers out there, not all of them can deliver both a holistic and granular viewpoint to the go-to-market team. Generic buyer intent data is no longer enough to survive in the digital marketing battlefield. It’s just one limited viewpoint with no flexibility to zoom in or map relationships. You need a better way of understanding and managing the very first entry points into your marketing funnel.
Before sharing what high-quality intent data looks like, let’s quickly set the stage with the frustrations fellow cybersecurity marketers face.
Meaningless data will drown your efforts
Being a cybersecurity marketer may be the most challenging specialty in tech marketing. You’re up against informed and distrusting buyers. And every campaign competes with a tidal wave of digital noise.
Startups with lean budgets tell us they’ve wasted precious dollars chasing cold, low-intent leads. Meanwhile, enterprise marketers—with more resources—still find themselves drowning in meaningless data.
So what’s broken in cybersecurity TOFU marketing?
We argue it’s an emphasis on volume above all else.

Traditional TOFU tactics still focus on casting wide nets—generating impressions, clicks, and vague form fills. But these metrics don’t translate to real pipeline. The funnel gets clogged with unqualified leads. Marketing and sales waste time chasing ghosts. It’s time to shift from obsessing on quantity to focusing on quality.
Traditional TOFU needs volume, and that's expensive and inefficent
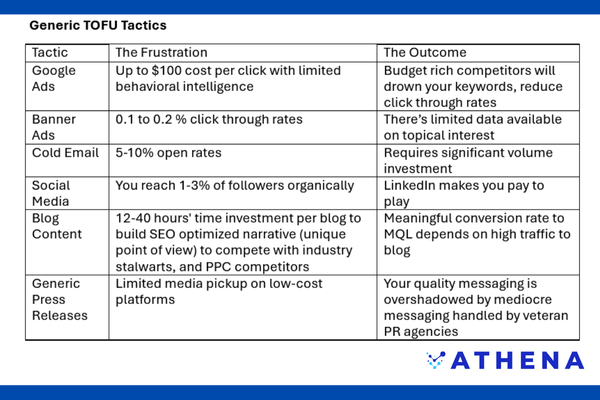
The table below summarizes why marketers are frustrated with generic top-of-funnel strategies. Notice the negative inverse relationships: as cost per click rises, click-through rates drop.
As targeting broadens, conversion quality shrinks. And as traffic volume increases, buyer relevance often disappears. In a nutshell, they can’t facilitate tracking of behavioral intelligence or buying intent.
So if generic top of funnel strategies are expensive and ineffiicent, what’s the smarter path forward?
Keep reading to find out!
Revisiting content syndication: the B2B gold standard for cybersecurity
Content syndication is the strategic distribution of your branded content—whitepapers, reports, webinars, and more—through trusted third-party publishers who already have the attention of your target audience. It flips the traditional model: instead of hoping buyers find your gated asset, you meet them where they already are, with the exact content that answers their pressing questions.

The benefit of working with ISMG is our deep expertise in content development. Our marketing advisory services team can help craft messaging/positioning and design assets you can put to market quickly.
In the cybersecurity sector, theaverage cost per raw Marketing Qualified Lead (MQL) from content syndication is around $65, making it a cost-effective method for acquiring potential customers. But modern syndication goes further than just reach and lead deliverability. Today, it’s about engagement visibility, lead qualification, and full-funnel continuity. Cybersecurity buyers don’t want fluffy content; they want depth, insight, and expert answers to their evolving challenges.
ISMG’s subscribers have spent over 2 billion minutes on our network. Nobody else has the same cybersecurity practitioner reach.
B2B marketers spend significant portions of their budgets to content marketing to differentiate, yet prospects often perceive messaging as repetitive or fear-based. Top-tier syndication partners can provide contact-level intent data that maps each buyer’s journey across multiple assets. That means marketers don’t just capture leads—they capture context, which powers smarter nurturing, better segmentation, and accelerated sales conversations.
We're giving you access to ISMG's black box of behavioral intelligence
We’ve been working on solving the intent data problem for cybersecurity marketers here at ISMG and have been getting positive results. Of course, we have an unfair advantage because of ISMG’s media network.
The solution is called Athena and it leverages our black box of first-party data not available anywhere else. Here’s a little overview of how we are creating contact level intent data for our fellow cybersecurity marketers.
It starts with a precision-targeted content syndication campaign, where cybersecurity assets—like threat reports, solution briefs, or webinars—are distributed across ISMG’s trusted media network to audiences actively engaging with your topical sweet spots.
Unlike traditional TOFU blasts, each asset engagement is tracked at the contact level, capturing behavioral signals across multiple touchpoints to build a detailed intent profile for every prospect.
As the campaign runs, high-intent leads are surfaced in near real-time, prioritized by factors like role, company fit, frequency of engagement, and topic alignment—ensuring you’re not just getting volume, but true buying signals.
Before any lead hits your CRM, it goes through Athena’s quality control process, which de-duplicates, enriches, and annotates leads with firmographic, behavioral, and campaign interaction data for sales-ready delivery.
Finally, your team receives a clean, actionable lead package directly into Salesforce or your CRM of choice, fully integrated and tagged by campaign, making it easy for BDRs to personalize outreach and accelerate conversations.
We built Athena because nobody else was providing the necessary granularity
Athena is ISMG’s secret weapon to getting contact level intent intelligence. The intent data is built on the backbone of our world class media network, with 15 million unique monthly touchpoints.
Our intent (no pun intended) isn’t to paint a grim picture of top-of-funnel marketing’s current state. The cybersecurity world is tough—and marketers often end up taking the blame when campaigns don’t deliver meaningful results. The reality is, today’s environment needs a bit of rehab. While many traditional awareness strategies will likely stick around (old habits die hard), relying on them repeatedly can erode reputation and dilute brand integrity over time.
The good news? Content syndication is thriving—because the buyers you want to reach crave unique narratives and love to dive deep into specific topics. Quality intent data helps you zero in on the most valuable prospects—the ones who are not only interested but who would benefit most from your solution. And the benefits don’t stop at demand generation. Product marketers also gain critical insights into what messages resonate and how the market is responding to specific features or positioning.
Another bright spot: many of us at ISMG have been in your shoes. We’re approaching this “rehab” with white-glove support—making it as smooth and frictionless as possible, without any painful withdrawal.
