Avoid the Smoke Machine

Why early-stage founders reward marketing performance art—and how “busy” cybersecurity marketers use it to hide from results.
Key Takeaways
-
Pressure to “show results” (especially post-funding) breeds marketing performance art
-
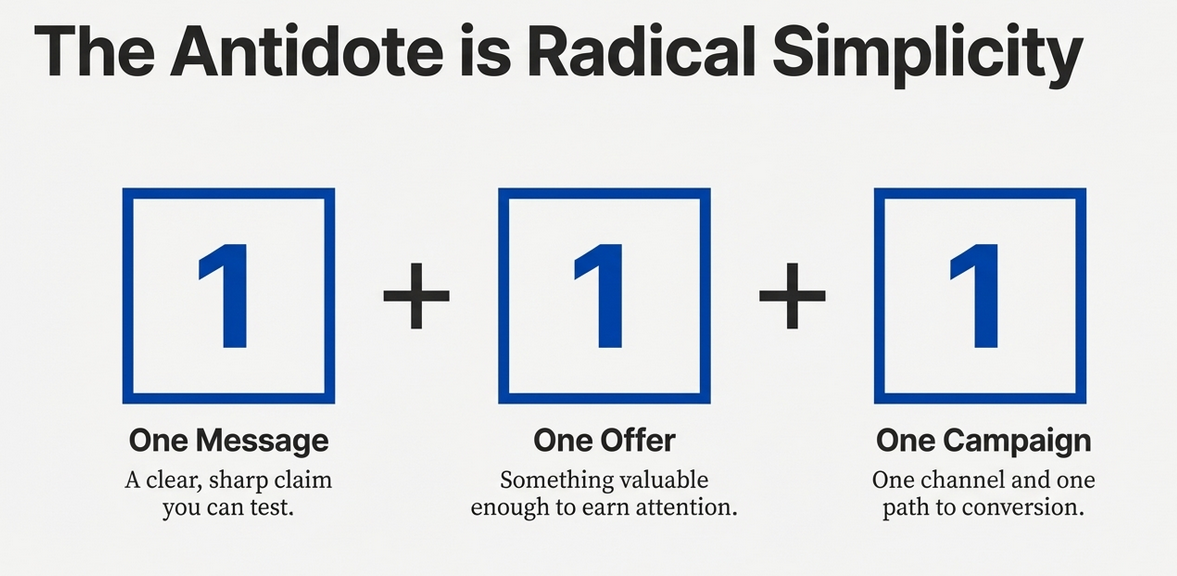
The real job is speed + focus: one message, one offer, one campaign
-
Measure one early outcome that matters: new sales conversations
-
Many generalist leaders hide behind volume and busywork to avoid accountability
-
The “smoke machine” looks strategic but delays truth; escape it with one thesis + tight experiments
Marketing ideas need breathing room
I once worked at a cybersecurity startup that had a true smoke-machine expert on the team. On Zoom calls, it felt like he had a microphone that doubled as a smoke machine: the moment he started talking, the room filled with verbal fog. People sat silent for seven to nine minutes at a time while he delivered monologues that sounded impressive but said almost nothing. Thank goodness for AI call-recording software. After those calls, I’d ask it to condense his monologues into a single sentence.
Here’s my favorite:
“I don’t know what to do yet, so I’m going to suggest doing everything.”
Cybersecurity marketing is one of the easiest functions to turn into a performance art piece because it’s often treated as subjective, hard to attribute, and easy to dress up with impressive language and eye candy. Off the record, that same marketing leader once told me:
“Let’s just throw everything at the wall and see what sticks.”
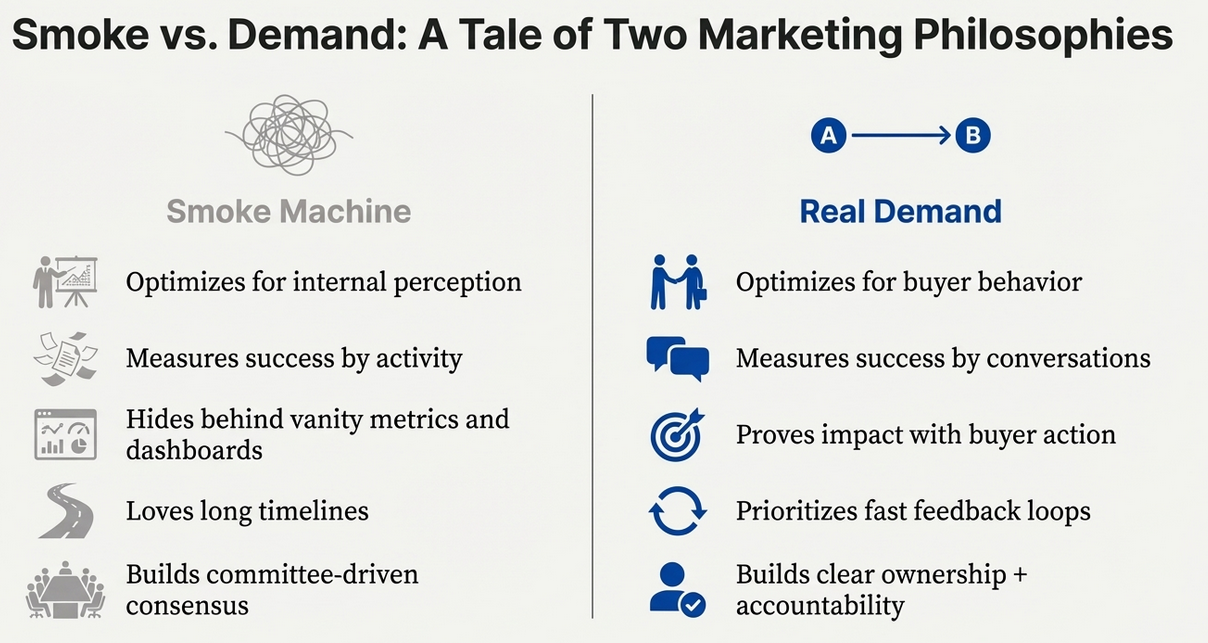
That’s the smoke machine in action. Busy calendars, polished slides, constant “strategy,” and endless motion—creating a haze that makes it hard to see the truth. None of it is translating into sales conversations.
Cybersecurity founders are smoke machine magnets
Cybersecurity founders face pressure from above and below. Investors want pipeline, while engineering wants resources and clear direction to build a quality product. But quality takes time, and iteration demands momentum, there’s no waiting for perfection. Most early-stage startups are sales and marketing organizations first; they have to acquire customers on good faith, winning over people who believe in the company’s future and are willing to take the bet. That means relentless leg work and finger work: in-person events, outbound follow-up, digital campaigns, and constant repetition. The goal is simple—grow customers, generate revenue, and use that money to invest back into product development and operational support.
That pressure makes founders vulnerable to a certain kind of “expert”: the one with a bucket of ideas, a hundred hats, and a pitch to do the job of multiple hires. They sound incredible in a meeting because they always have another initiative to propose. But it’s rarely what you actually need. Their real skill is buying time—by creating motion, complexity, and unfinished work that looks like progress. Months later, you’re left with half-built projects, a bloated roadmap, and the same problem you started with: not enough pipeline. This is the profile to avoid.
Avoiding cybersecurity smoke machinists
Some cybersecurity marketers build an entire career around performance art. They have optimized their day to day activities for surviving inside founder anxiety and investor pressure. They know how to create motion, noise, and complexity that feels like strategy while delaying accountability.
Here are the five things they do:
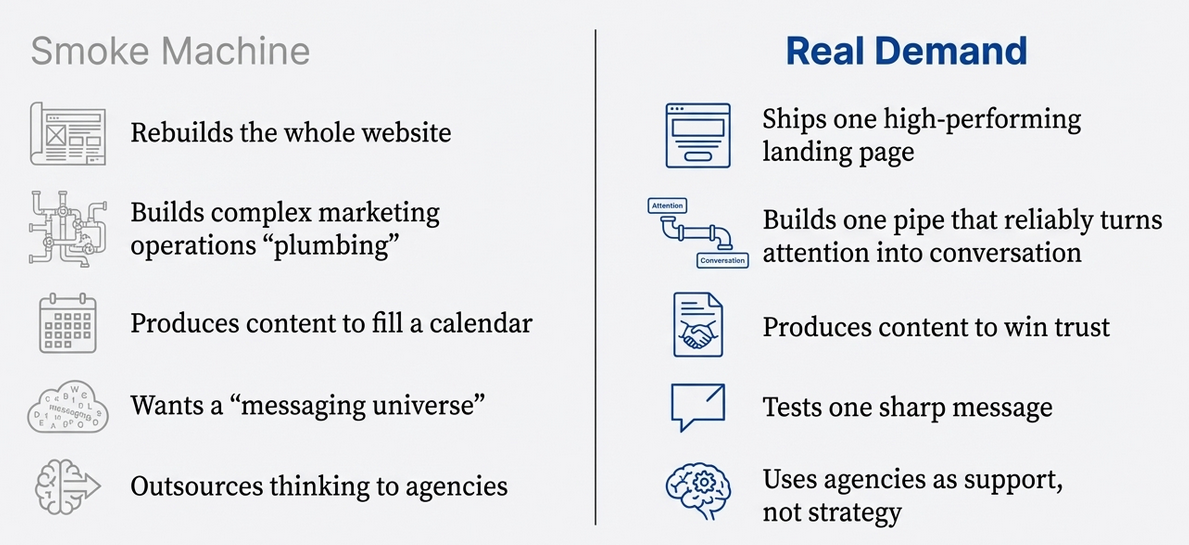
- Run endless messaging workshops instead of choosing one message.
They create “positioning universes,” persona maps, and 20-slide narrative decks so nobody ever has to commit to a clear claim that can be tested. - Launch long timelines that delay accountability.
Everything takes a quarter. Then two quarters. Big initiatives like rebrands, category design, or “strategic GTM alignment” create the illusion of progress while postponing results. - Hide behind vanity metrics and dashboards.
Impressions, engagement, follower growth, traffic, downloads—numbers that look good in a board update but don’t turn into sales conversations. - Recommend complexity too early.
They push website rebuilds, marketing ops plumbing, lead scoring, automation workflows, multi-stage funnels—building a cathedral of pipes instead of one simple path from attention to conversion. - Stay busy across too many projects and too many channels.
They scatter effort across webinars, podcasts, SEO, paid, ABM, events, newsletters, partnerships—creating “activity” that makes it hard to pinpoint what’s working and even harder to assign blame when nothing works.
The end result is always the same: polished slides, full calendars, constant “strategy,” and very few new sales conversations. The smoke machine isn’t the absence of effort. It’s effort designed to create cover.

Less pollution makes it easier to see the market
Real cybersecurity marketing is simple—and that’s why it’s so uncomfortable. You need:
- One message (a clear, sharp claim you can test)
- One offer (something valuable enough to earn attention)
- One campaign (one channel and one path to conversion)
Then you run tight experiments until it works. Not to “scale” immediately, but to validate reality: Do buyers click? Do they convert? Do they talk to sales?
The early-stage metric that keeps you out of theater is also the simplest: conversations. If marketing isn’t producing sales conversations, it isn’t working. Full stop.
Marketing smoke thrives because it creates motion without vulnerability. Real marketing requires choosing one angle and risking being wrong in public. But that’s the whole point: you choose, test, learn, and iterate—fast enough to adjust before you waste a quarter.
The winners in 2026 won’t be the companies with the most content, the biggest stack, or the prettiest website. They’ll be the ones with the clearest truth, the strongest voice, and the discipline to repeat one campaign until it produces conversations.