Take the Guesswork out of Cybersecurity Marketing.
Athena for sales
From targeting new accounts and nurturing existing to prioritizing engagements and managing pipelines, Athena empowers sales with data-driven insights to inform every stage of the sales journey.
Learn more
Athena for marketing
Identify the right buying teams earlier using contact-level intelligence (CLI). Activate ISMG channels your audience already trusts, to nurture buying teams over time and earn a place on day-one shortlists.
Learn more
Athena case studies
“We knew someone at JPMorgan was researching our product category…but who? Hundreds of people fit our ICP. How were we supposed to follow-up?”
Two case studies explore CLI’s impact on client pipeline.
Download case study
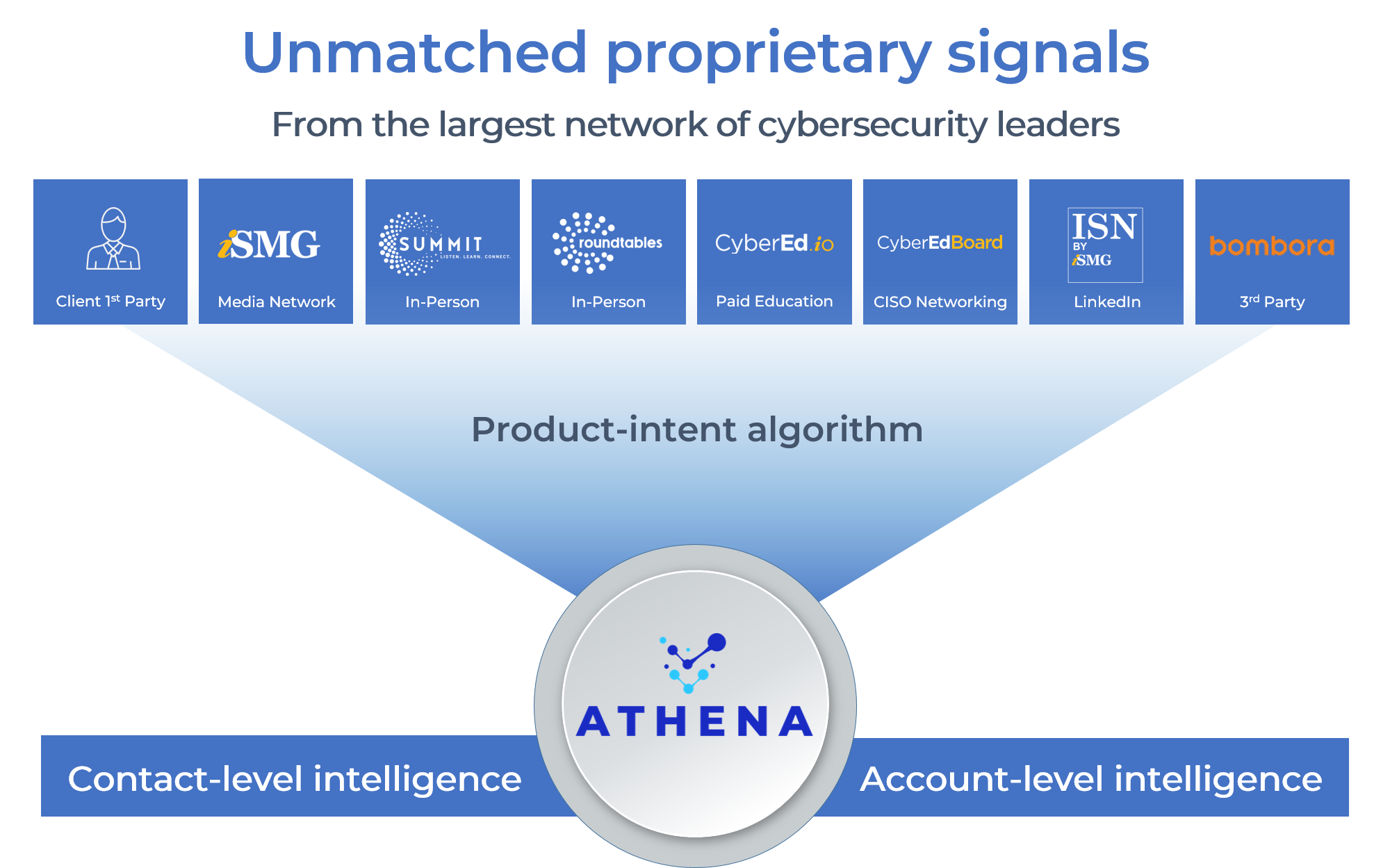
Reliable contact-level intelligence
built on unmatched first-party data
Athena is built on proprietary first-party signals from cybersecurity leaders’ real behavior across ISMG’s ecosystem.
It captures what leaders read and research across ISMG’s media network, what priorities get debated and validated at executive events, what’s top-of-mind inside major enterprises through private CISO communities, and what organizations consume through ISMG’s CyberEd training platform to build skills and close gaps.
The result is a higher-quality foundation of intent data that drives the right outreach at the right time.
Account-level signals hide the people who actually decide
Real decisions are made by buying groups, not anonymous accounts. Understanding who those buyers are, requires contact-level visibility.
38 media properties | 500k daily audience interactions | 400 in-person events
Athena tackles your biggest ABM challenge
Enhance your Revenue Pipeline with Athena’s Contact-Level Intelligence. Athena's compelling combination of proprietary publisher signals, laser-focused keyword capture, and the unrivalled power to decipher behavioral intent at the contact and buying group level is tailored to meet your biggest ABM challenge.
Influence the invisible cybersecurity buyer
Tap into opportunities that weren’t previously visible. Shape buyer perception before they have formed strong opinions about which vendors they’ll short-list.
In this on-demand interview, ISMG leaders Ron Glucksman, Managing Director of Growth Strategy, and Anna Delaney, Executive Director of Productions, unpack the new realities of cybersecurity marketing — where traditional funnels no longer capture how modern buyers make decisions.
Flexible by design: Use Athena your way
Athena is available as a self-serve platform and as a fully managed service led by ISMG market experts.
Whether your team wants hands-on control or expert-led execution, Athena adapts to your needs without forcing you into new workflows or tools.

Speak with the team
Ready to experience the power of Athena for yourself?
Discover how Athena helps cybersecurity go to market teams
Read the latest thought leadership and case studies from the Athena team