Get More Cybersecurity Buyers Talking to You
Guidance for every step of the cybersecurity marketing cycle
From strategy to execution, we’ll get your ideas resonating with the cybersecurity world.
Strategy
We’ll build a framework that’s authentic to your buyer’s needs with measurable reporting.
- Messaging/Positioning
- Persona testing
- Content strategy
- Intent data targeting
Creative
No cookie cutter design or copycat deliverables allowed when working with us.
- Branding
- Visual identity
- Website design
- Marketing asset creation
Execution
Professionals to support those time-consuming areas that require niche expertise
- Media planning /buying
- Email/social media management
- Search (SEO/SEM)
- Public relations

Marketing agency built by CISO visionaries.
We were the world's first marketing advisory firm built from the ground up by CISOs. Today, hundreds of cybersecurity organizations trust us to help them go to market and drive revenue. Our professionals leverage insider intelligence and proprietary data models for optimal outcomes.
Learn More about CyberTheory

Marketing operations experts with a security soul
Xtra mile is a global B2B lifecycle marketing agency specializing in transforming customer engagement from acquisition to retention, particularly within the hi-tech and industrial sectors. Our lifecycle marketing approach is all about the value a company brings to all its shareholders.
Learn more about Xtramile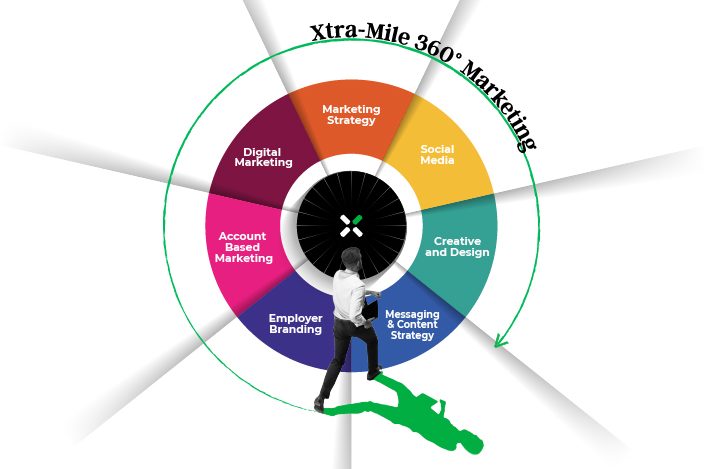
When you need something more cyber than a Madison Avenue marketing agency
Intellectual capital support
Use our specialized playbooks, battle-tested by practitioners, whether you need an extra hand or an entire auditorium.
CISO Advisory Panel
Pressure-test your messaging and positioning before it hits the market so you don’t waste resources.
Sales knowledge transfer
Ensure your campaign tactics lead to better human sales interaction so the go-to-market team can go beyond.
Media production powerhouse
World-class editorial and creative teams craft media that cybersecurity professionals love and trust—since 2006.
Intelligence on 2M security practitioners
Get access to ISMG intent data that’s so granular you can make your marketing decisions human to human.

Proven track record
Hundreds of happy clients trust us to help them tackle their most challenging cybersecurity marketing endeavors
Latest resources
Learn how to plan your cybersecurity marketing strategy and campaign activities.